This is a follow on from a previous guide where I showed how to setup Kerberos and NTLM Proxy Authentication on the FortiGate.
This guide aims to build on that and setup firewall rules to push a transparent Web Filter Profile to users that do not configure the proxy on their desktops or don't authenticate.
This may be useful for a network where you have a mix of domain joined and personal devices on a network (not something we would want happening but you get the picture)
For this to make sense, you should have followed this guide already and be at the point where web filtering is working for the different groups.
Firstly, we need to create a Web Filter Profile for transparent access. You can create one under 'Security Profiles' and then 'Web Filter'.
Here is an example of mine:
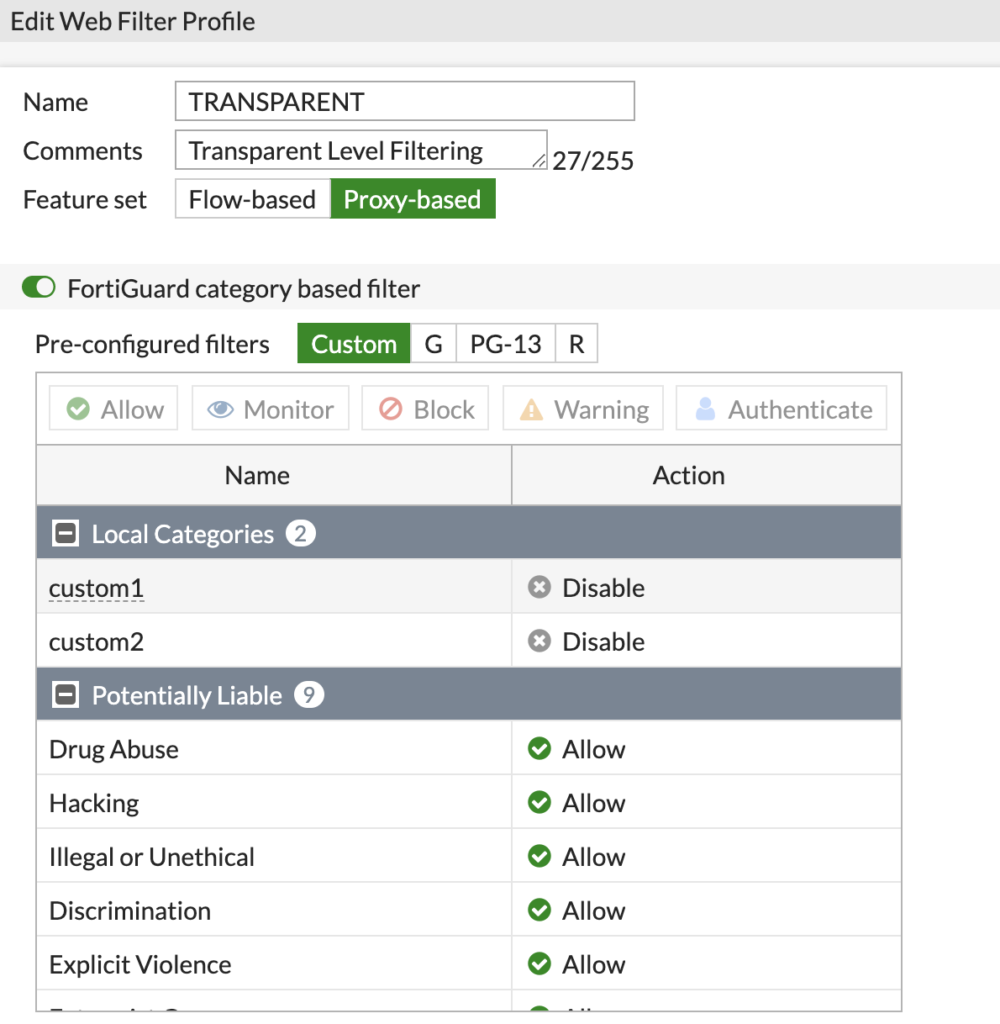
The 'Feature set' is still set to Proxy-based. However, the policy won't be applied via a Proxy Policy. This allows us to use the rule later on in the future in a Proxy Policy if we need to.
Now the Web Filter Profile is created, we need to configure the Firewall Policies to use it.
Navigate to 'Firewall Policy' under 'Policy & Objects'.
Its a good idea to split your Web Filter policy like this:
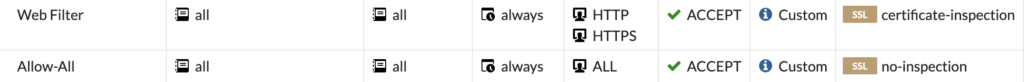
Having them split will allow you to only make changes to the web traffic and not cause unnecessary inspection on non-web traffic.
Click on your Web Filter policy and edit it. At the moment, mine looks like this:
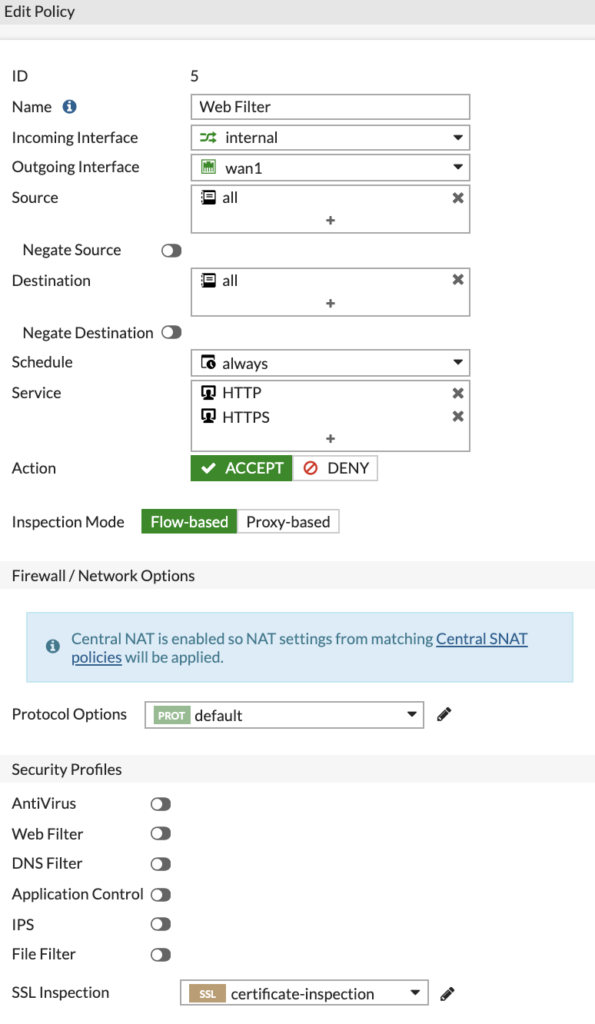
This is just a base rule with no settings other than SSL Inspection applied.
To transparently filter traffic for devices that have not authenticated with the FortiGate, we need to switch the 'Inspection Mode' to 'Proxy-based' and turn on the 'Web Filter' option and select the Transparent profile.
If you don't change the inspection mode, you will not see the Web Filter Profile we created before.
When finished, the profile should look like this:
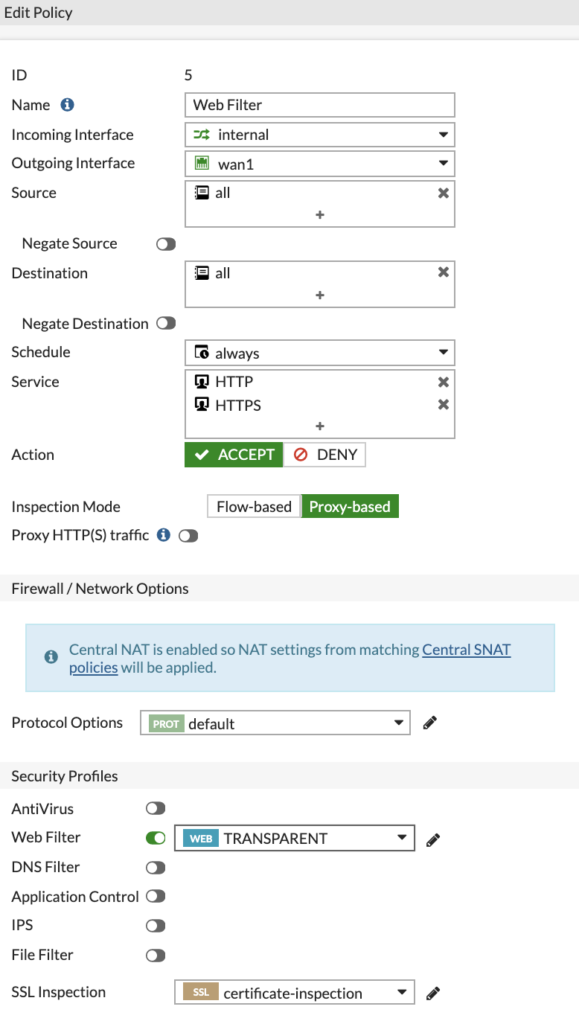
We don't want the traffic to be pushed onto the proxy so we leave the 'Proxy HTTP(S) traffic' slider off. If this was on, users that were accessing transparently would see authentication popups. Which defeats the object of trying to access transparently.
If we save this Policy now, the list should look like this:

You must ensure the specific HTTP and HTTPS policy is above the less specific rule.
If we go back to one of our Domain Joined clients now and remove the proxy configuration:
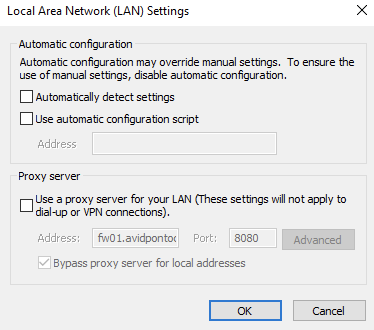
If we visit a site that should be blocked by the Transparent web filter profile, we see it gets blocked and shows the correct profile in the logs:
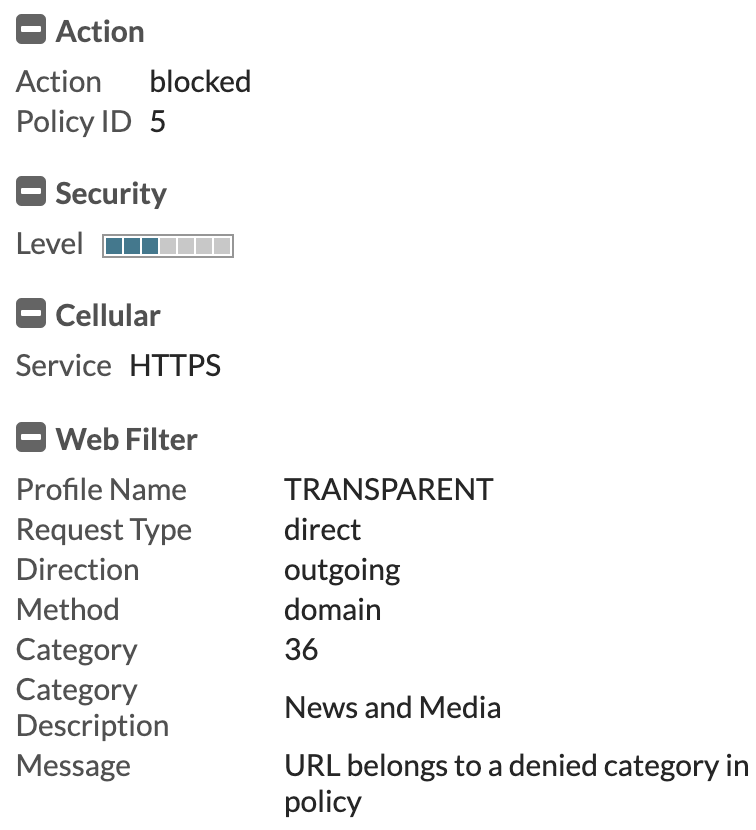
We also note that no authentication challenges were shown for the device.
If we enable the proxy again:
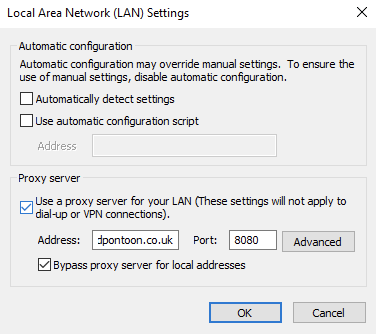
If we visit a site that should be blocked by the group based proxy policy for this users group, we see it gets blocked and shows the correct profile in the logs:
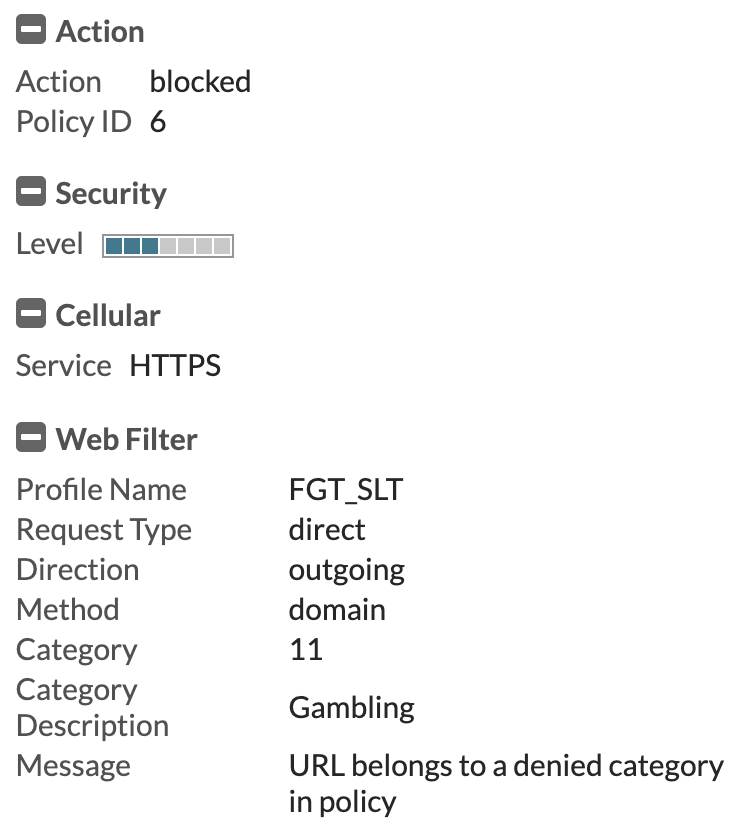
You now have a functioning environment that will catch any devices that do not authenticate with the FortiGate and give them a more strict level of filtering as a failsafe. However, when a device does authenticate, it gets the correct policy based on that users group assignment within Active Directory.

0 Comments