As we have exhausted all IPv4 addresses it was decided to implement NAT in a lot of areas of the internet. You are probably reading this sat behind a router that is performing a variation of NAT.
NAT's purpose is to translate addresses. The main example of this would be ISP customers, they will have a private address space behind the router - corresponding with RFC1918 which gets translated to a public IP address for use on the internet. This would mean that ISP customers can all use the same subnet behind their routers, and not have to worry about overlapping with another customer.
Cisco have a technology called PAT, this allows many internal IP addresses to be translated to one single public IP address with ease. You can also configure a pool of external addresses.
Lets look at how to configure it. Here is the topology:
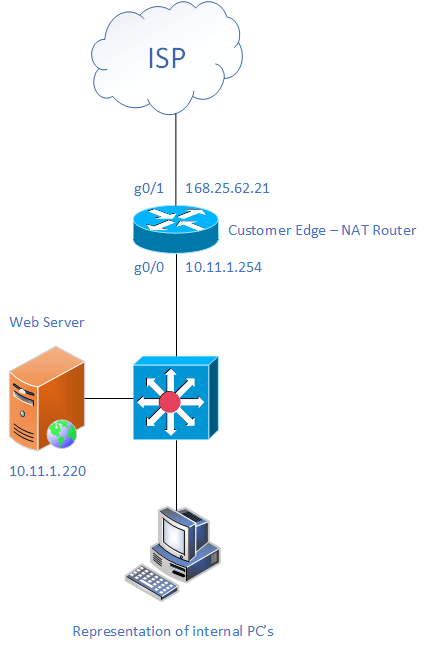
Here we will configure PAT on the Customer Edge router
First we need to indicate which is our internal and external interfaces, this is self explanatory:
Customer_Edge(config)# interface GigabitEthernet 0/0
Customer_Edge(config-if)# ip nat inside
Customer_Edge(config)# interface GigabitEthernet 0/1
Customer_Edge(config-if)# ip nat outsideNow we need to create at Access Control List to specify the traffic that we want to translate. For the network above, we would use this ACL:
Customer_Edge(config)# access-list 1 permit 10.11.1.0 0.0.0.255Now we have these two parts done, we need to tie them together with one command:
Customer_Edge(config)# ip nat inside source list 1 interface GigabitEthernet 0/1 overload
Where '1' is the ACL number and 'GigabitEthernet 0/0' is the outbound interfaceAfter this command has been inputted, all your private addresses internal will be translated to the public IP address configured on the external interface.

0 Comments