In this part we are going to look at the L2VNI setup of the topology. This is basically the VLAN setup of the topology where we can define the vlans in use.
Lets remind ourselves of the topology:
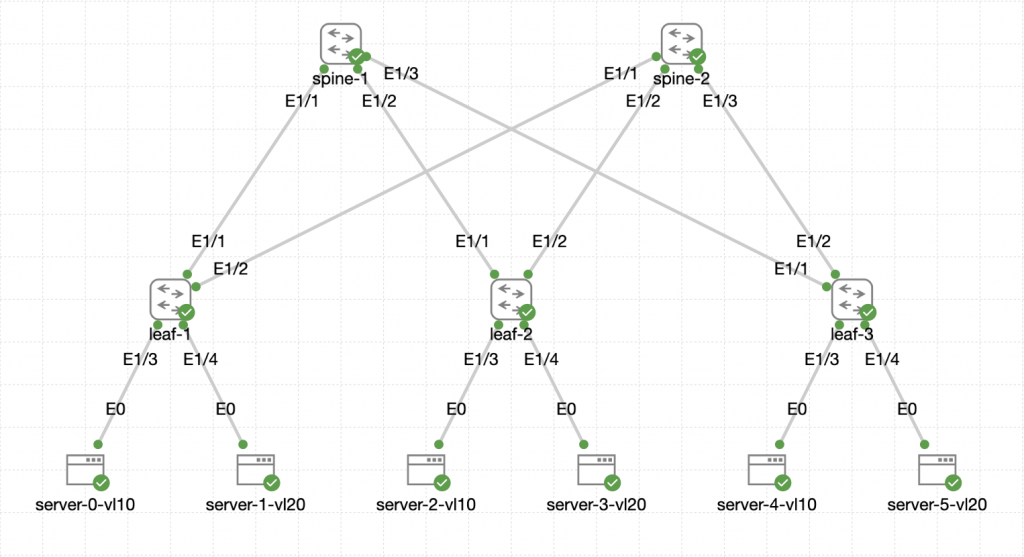
The L2VNI setup is isolated to the leaves as the spines are not involved and are not specifically configured with the underlaying VNI setup.
L2VNI Configuration
In our topology, we have servers in vlan 10 and vlan 20. By the end of this part, the servers on the same vlan will be able to communicate at layer 2 despite being separated by layer 3 boundaries.
The L2VNI configuration is nice and simple and means it can be replicated for as many layer 2 domain as your needs require.
Lets look at vlan 10 first:
vlan 10
vn-segment 100010
interface nve1
member vni 100010
suppress-arp
mcast-group 224.1.1.192
evpn
vni 100010 l2
rd auto
route-target import auto
route-target export autoThe configuration above creates the vlan and assigns the vn-segment ID for the vlan, this should match across the topology for this vlan. Next, we add the vni into the nve interface and add the command to suppress arp, this is a very useful command which allows the leaves to cache mac addresses of nodes attached to prevent excessive ARP messages being sent across the fabric.
The last part of the configuration adds the vni to the evpn control plane so it can be pushed into the MP-BGP topology.
Lets also quickly add the configuration for vlan 20 too on all leaves:
vlan 20
vn-segment 100020
interface nve1
member vni 100020
suppress-arp
mcast-group 224.1.1.192
evpn
vni 100020 l2
rd auto
route-target import auto
route-target export autoAs you can tell, the configuration is very similar to add new L2VNIs.
Verification
We should in theory now have layer 2 communication between the servers, lets test that fact between server-0 and server-2:
server-0-vl10:~$ ping 10.10.1.2
PING 10.10.1.2 (10.10.1.2): 56 data bytes
64 bytes from 10.10.1.2: seq=0 ttl=42 time=36.515 ms
64 bytes from 10.10.1.2: seq=1 ttl=42 time=8.598 ms
64 bytes from 10.10.1.2: seq=2 ttl=42 time=8.448 ms
64 bytes from 10.10.1.2: seq=3 ttl=42 time=6.798 ms
^C
--- 10.10.1.2 ping statistics ---
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max = 6.798/15.089/36.515 msSuccess! we have layer 2 connectivity. Lets do a few commands to confirm whats happening.
We can check the arp cache on the leaves to show the flood and learn technique in action:
leaf-1# show ip arp suppression-cache vlan 10
Flags: + - Adjacencies synced via CFSoE
L - Local Adjacency
R - Remote Adjacency
L2 - Learnt over L2 interface
PS - Added via L2RIB, Peer Sync
RO - Dervied from L2RIB Peer Sync Entry
Ip Address Age Mac Address Vlan Physical-ifindex Flags Remote Vtep Addrs
10.10.1.1 00:02:06 5254.000a.ded9 10 Ethernet1/3 L2
10.10.1.2 00:02:06 5254.001f.2d39 10 (null) R 10.0.0.4 We can see from leaf-1 we have 10.10.1.1 (server-0) learnt locally and then 10.10.1.2 (server-2) learnt remotely from the remote vtep of 10.0.0.4 which is leaf-2 and is where server-2 is connected.
We can also check the BGP l2vpn evpn table for the address 10.10.1.2 on leaf-1:
leaf-1# show bgp l2vpn evpn 10.10.1.2
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 10.0.0.3:32777 (L2VNI 100010)
BGP routing table entry for [2]:[0]:[0]:[48]:[5254.001f.2d39]:[32]:[10.10.1.2]/248, version 15
Paths: (1 available, best #1)
Flags: (0x000212) (high32 00000000) on xmit-list, is in l2rib/evpn, is not in HW
Advertised path-id 1
Path type: internal, path is valid, is best path, no labeled nexthop, in rib
Imported from 10.0.0.4:32777:[2]:[0]:[0]:[48]:[5254.001f.2d39]:[32]:[10.10.1.2]/248
AS-Path: NONE, path sourced internal to AS
10.0.0.4 (metric 81) from 10.0.0.1 (10.0.0.1)
Origin IGP, MED not set, localpref 100, weight 0
Received label 100010
Extcommunity: RT:64500:100010 ENCAP:8
Originator: 10.0.0.4 Cluster list: 10.0.0.1
Path-id 1 not advertised to any peer
Route Distinguisher: 10.0.0.4:32777
BGP routing table entry for [2]:[0]:[0]:[48]:[5254.001f.2d39]:[32]:[10.10.1.2]/248, version 14
Paths: (2 available, best #1)
Flags: (0x000202) (high32 00000000) on xmit-list, is not in l2rib/evpn, is not in HW
Advertised path-id 1
Path type: internal, path is valid, is best path, no labeled nexthop
Imported to 1 destination(s)
Imported paths list: L2-100010
AS-Path: NONE, path sourced internal to AS
10.0.0.4 (metric 81) from 10.0.0.1 (10.0.0.1)
Origin IGP, MED not set, localpref 100, weight 0
Received label 100010
Extcommunity: RT:64500:100010 ENCAP:8
Originator: 10.0.0.4 Cluster list: 10.0.0.1
Path type: internal, path is valid, not best reason: Neighbor Address, no labeled nexthop
AS-Path: NONE, path sourced internal to AS
10.0.0.4 (metric 81) from 10.0.0.2 (10.0.0.2)
Origin IGP, MED not set, localpref 100, weight 0
Received label 100010
Extcommunity: RT:64500:100010 ENCAP:8
Originator: 10.0.0.4 Cluster list: 10.0.0.2
Path-id 1 not advertised to any peerNow, thats a lot of output. But, lets break it down. We can see the top route is attached to the RD 10.0.0.3:32777. We can see that it was imported from the RD 10.0.0.4:32777 which is leaf-2. This makes sense because the route originated from 10.0.0.4. The reason there is only a single route within 10.0.0.3:32777 is because only a single route from the leaf-2 RD was marked as Best and that was the one that was imported. We can verify that by looking at the Cluster list. This is the RID of the Route Reflector.
We can also see the MAC address and IP address of server-2 in the entry to confirm its the correct mapping.
There will be an entry on leaf-2 for the IP-MAC mapping for server-0 for the return traffic.
Note - The mac addresses are learnt as normal so a host has to communicate on the network for the leaf to grab its MAC address and advertise it. This is the role of arp suppression in flood and learn.
In the next part we will look at setting up anycast gateways for the L2VNIs so we can start the process of getting the hosts of their layer 2 network.

0 Comments