In the last part, we got a single tenant VRF working, in this part, we will look at splitting vlan 20 off into its own separate Tenant to show a multi-tenant setup.
Lets remind ourselves of the topology:
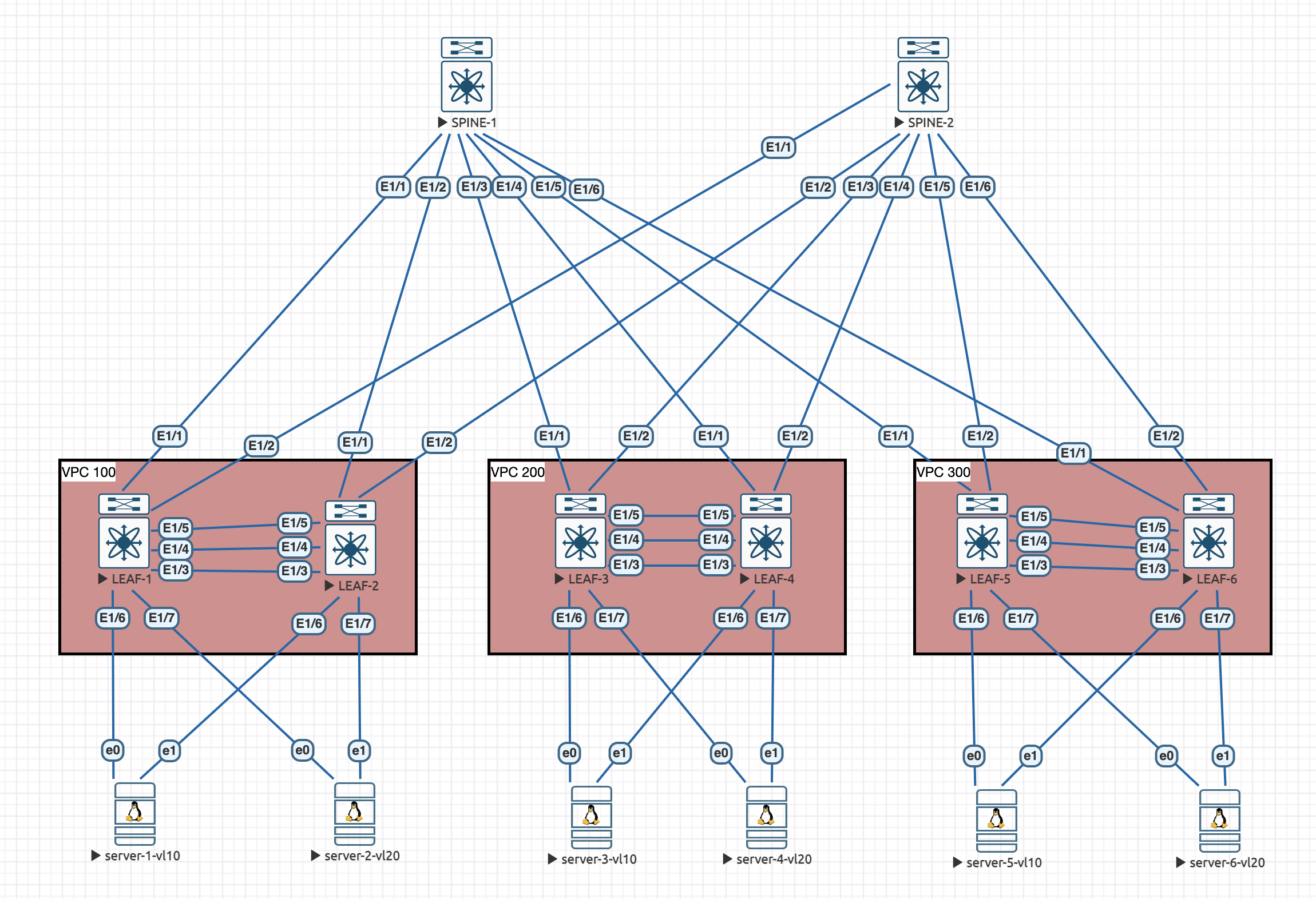
I have added more servers into the topology since last time to be able to properly simulate the multi-tenancy.
All of the configuration below is for the Leaves in the topology.
Vlan Configuration
Before we begin, with the addition of the other servers, we need to make sure all the VNIs are on all of the leaves and they are mapped to the correct interfaces. Po2 on each switch goes to the vl10 server and Po3 to vl20:
vlan 10
vn-segment 100010
vlan 20
vn-segment 100020
interface nve1
member vni 100010
suppress-arp
mcast-group 224.1.1.192
member vni 100020
suppress-arp
mcast-group 224.1.1.192
evpn
vni 100010 l2
rd auto
route-target import auto
route-target export auto
vni 100020 l2
rd auto
route-target import auto
route-target export auto
interface port-channel2
switchport access vlan 10
interface port-channel3
switchport access vlan 20Firstly, we need to configure another L3VNI vlan for the routing in this new tenant, this configuration is for the leaves:
vlan 998
vn-segment 100998VRF Configuration
We also need another tenant VRF to be configured which will house the overlay routing:
vrf context OVERLAY-TENANT2
vni 100998
rd auto
address-family ipv4 unicast
route-target both auto
route-target both auto evpnThis configuration also brings in the EVPN information too.
We should also move the SVI for Vlan 20 over to the new VRF and add the Layer 3 info back in:
interface Vlan20
vrf member OVERLAY-TENANT2
ip address 10.2.1.254/24
fabric forwarding mode anycast-gatewaySVI and NVE Configuration
We also need to setup a new L3VNI SVI on the Leaves. This is a duplicate of what Vlan999 was used for in the last part. With multi-tenant setups we need a separate L3VNI for it:
interface Vlan998
no shutdown
vrf member OVERLAY-TENANT2
ip forwardWe also need to add the VNI to the original nve interface:
interface nve1
member vni 100998 associate-vrfBGP Configuration
The final part is the BGP configuration, we need to put in the new VRF but also make sure we remove the vlan 20 network from being advertised in the other VRF:
router bgp 64500
vrf OVERLAY-TENANT1
address-family ipv4 unicast
network 10.1.1.0/24
vrf OVERLAY-TENANT2
log-neighbor-changes
address-family ipv4 unicast
network 10.2.1.0/24Verification
At this point, we need to give BGP some time to converge and then we can see the separate BGP tables:
LEAF-1# show bgp ipv4 unicast vrf OVERLAY-TENANT1 | beg Network
Network Next Hop Metric LocPrf Weight Path
* i10.1.1.0/24 10.0.1.6 100 0 i
* i 10.0.1.5 100 0 i
* i 10.0.1.4 100 0 i
* i 10.0.1.3 100 0 i
* i 10.0.1.2 100 0 i
*>l 0.0.0.0 100 32768 i
*>i10.1.1.2/32 10.0.1.102 100 0 i
* i 10.0.1.102 100 0 i
* i10.1.1.3/32 10.0.1.103 100 0 i
*>i 10.0.1.103 100 0 i
LEAF-1# show bgp ipv4 unicast vrf OVERLAY-TENANT2 | beg Network
Network Next Hop Metric LocPrf Weight Path
* i10.2.1.0/24 10.0.1.4 100 0 i
* i 10.0.1.3 100 0 i
* i 10.0.1.2 100 0 i
*>l 0.0.0.0 100 32768 i
* i 10.0.1.6 100 0 i
* i 10.0.1.5 100 0 i
*>i10.2.1.2/32 10.0.1.102 100 0 i
* i 10.0.1.102 100 0 i
* i10.2.1.3/32 10.0.1.103 100 0 i
*>i 10.0.1.103 100 0 iHere we can see that Leaf-1 knows about 10.2.1.0/24 (Vlan20) from all the other leaves, and its being locally originated.
We should still have layer 2 connectivity within the VNIs but we should have broken layer 3 connectivity between the two vlans because they reside in separate tenants:
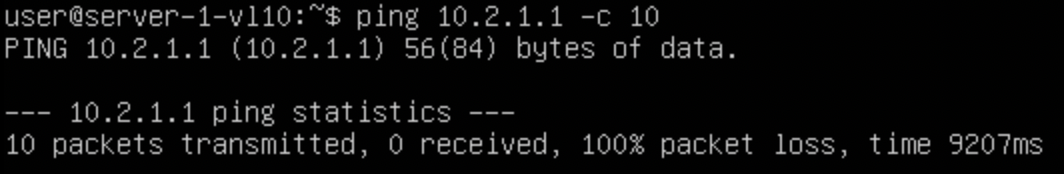
This is what we expected, the tenants are now separate. However, there are ways to regain communications between the networks despite them being in different tenants. This may be required in some topologies. We will explore this in the next part.

0 Comments